Keep control over your corporate data on users’ personal devices
As your organization moves to the cloud and users become more mobile than ever, the device landscape changes as well. End users are always connected and use a wide variety of devices, ranging from laptops and tablets to smartphones. Bring your own Device (BYOD) strategies are being widely adopted.
Device management already earned its marks when it comes to the ease of enrolment of new devices, managing configuration policies, and so on. Also, from a cyber security and information protection point of view, a device management strategy can and will empower your security strategy and execution. But the management of personal devices isn’t always an easy sell within an organization – employees are often reluctant to have their personal device managed by their employer. Luckily, there is MAM…
What is MAM?
Microsoft Application Management (MAM) is a strong feature that helps companies secure corporate data on mobile devices. MAM doesn’t require the device to be managed by Endpoint Manager (Intune). Therefore MAM is often used in BYOD scenarios, as end users don’t like the fact that their personal device is managed by their employer. That being said, MAM still has additional value in securing corporate data even when the device is not fully managed.
How does it work?
MAM enables companies to set app protection policies which will protect the company data in the apps. These policies include the following:
- Data relocation policies which limit the user from saving copies of company data and restrict copy/paste between company and private data
- Access policy settings which require the user to enter a PIN code to access the app
- Preventing managed apps from running on jailbroken or rooted devices
If the app protection policies are set, the company data is separated from the personal data within the app itself. In the picture below you can see that the corporate data is stored in an encrypted container to which only the managed applications have access. Third party apps will not have access to corporate data unless it’s specifically allowed. This can all be done without registering the device in Endpoint Manager.
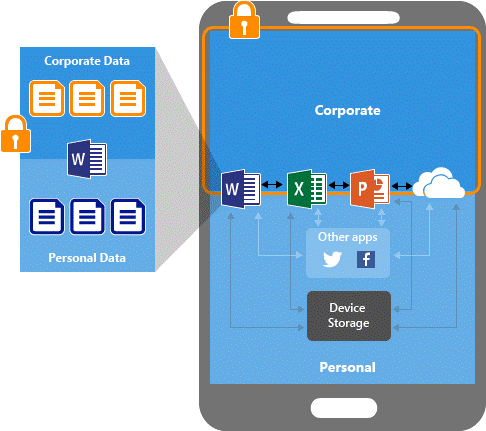
A complete list of apps supporting MAM can be found here. Companies who built their own app can use Intune SDK or wrap the app with the Intune App Wrapping Tool to enable the app protecting policies.
New conditional access policy
Microsoft released a new conditional access policy – which is currently still in preview – to enforce that the app has protection policies before access is allowed to the cloud apps.
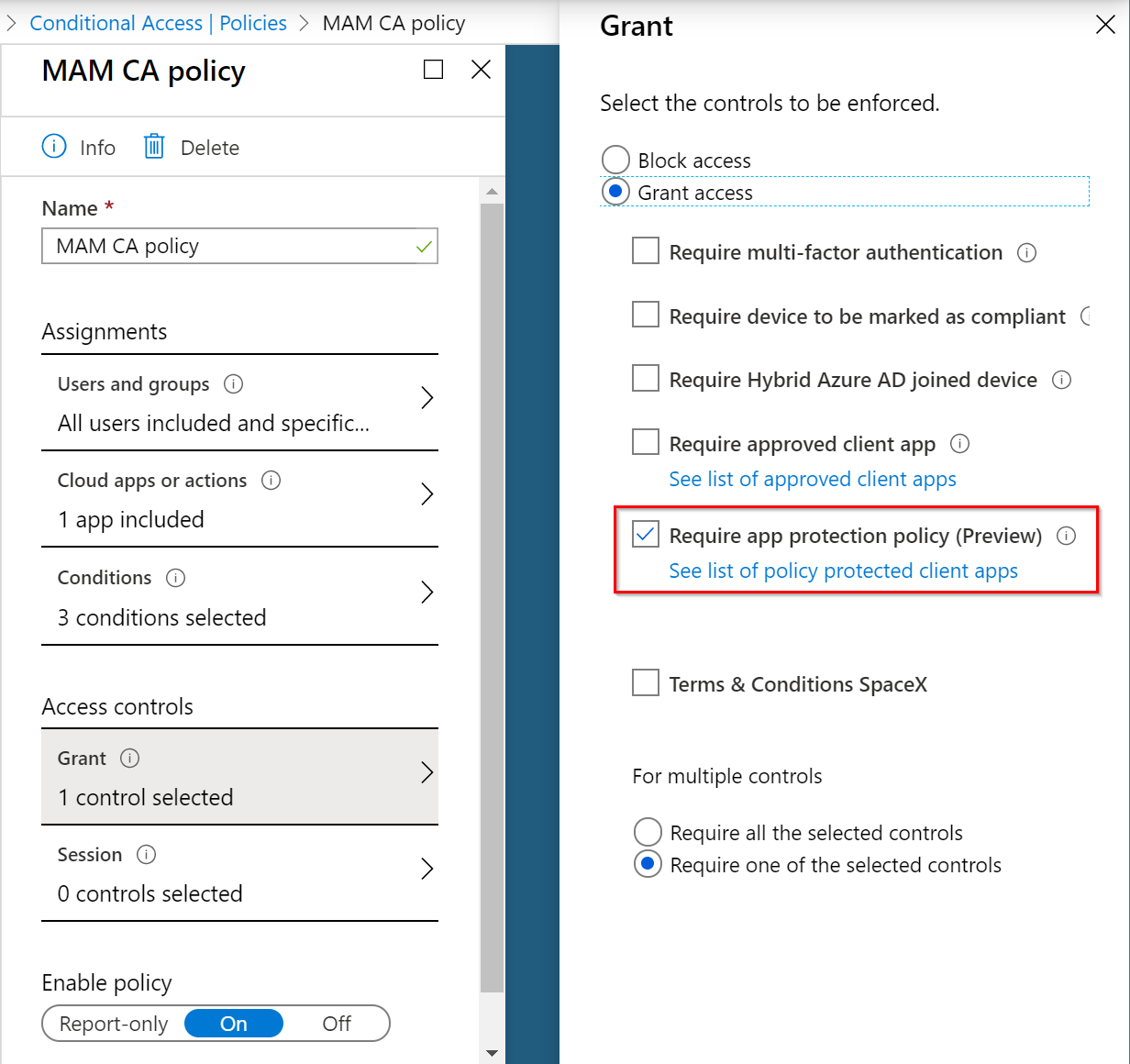
Setting this conditional access policy is only one part of the configuration. Before you can apply conditional access to a device, it needs to be registered in Azure AD. This registration is done by a broker app on the device, which is different for each mobile operating system. iOS uses Microsoft Authenticator and Android uses the Intune Company Portal app.
Since the mobile devices aren’t managed by Endpoint Manager, it’s not possible to deploy these broker apps to the devices. When the conditional access policy is applicable, and the app is trying to connect to one of the cloud apps, the user is guided to install the broker app.
Android users are requested to install the Company Portal app. After being installed, it will register the device in Azure AD:
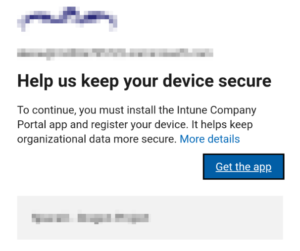
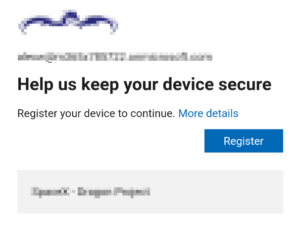
For iOS users, the experience is similar:
The result is that these devices are registered in Azure AD separately, and not joined together in Mobile Device Management (MDM).

Now the conditional access policy can be applied to these devices.
As mentioned above, the conditional access policy for MAM is still in preview, so currently only the following apps are supported:
- Microsoft Cortana
- Microsoft OneDrive
- Microsoft Outlook
- Microsoft Planner
It is safe to assume that other Microsoft applications will be added to this list.
Summarizing, companies can enforce users to use MAM-enabled apps on BYOD devices, without the device being fully managed by Endpoint Manager (or any other MDM solution).

